Image Copyright © BluOcean Digital 2023This image depicts a digital battlefield with symbols of evolving technology and cybersecurity threats. In the foreground, a group of strategists are transitioning from a control-based approach (represented by static defensive structures) to a risk-based approach (represented by dynamic, adaptable defenses). The overall tone of the image conveys the shift from reactive to proactive strategies in cybersecurity.
Picture this: a battlefield, not of physical might, but of digital prowess. The terrain is ever-changing, morphing under the weight of relentless innovation. New adversaries emerge from the fog of war, their weapons not of steel but of code and cunning.
This is our reality in cybersecurity.
We stand on the front lines, our digital assets behind us, facing an enemy that improves with each passing second. Every day, we strategize, adapt, and fortify our defenses, knowing that the battle for digital security is a war without end.
But as we stand our ground on this digital battlefield, we must acknowledge that yesterday’s strategies may not serve us in tomorrow’s wars. Traditionally, many organizations have adopted a control-based approach to cybersecurity, focusing on implementing specific security measures to protect against known threats.
As technology rapidly evolves, with the emergence of cloud platforms, artificial intelligence, and SaaS, we find ourselves navigating an increasingly complex and volatile cybersecurity landscape compounded by a globally diverse data security and privacy regulatory environment.
Traditional control-based maturity models are grappling with these swift technological changes. Their primary approach, which involves increased investment in tools and controls, fails to provide a clear return on investment or demonstrate a tangible reduction in risk to the company. According to a recent IBM survey, organizations utilizing over 50 security tools rated their ability to detect and respond to an attack lower than those using fewer tools. Furthermore, 60% of respondents cited reduced cyber resilience due to a lack of visibility into applications and data assets. This shift towards a business-defined risk-based approach is becoming increasingly necessary to secure the business and companies in alignment with management, stakeholders, and boards’ risk appetite. This article provides a 4-step actionable blueprint on how organizations can transition from a control-based to a risk-based cybersecurity program and the challenges they might face during this transition.
Understanding the Shift
Before delving into the transition process, it’s crucial to understand the fundamental differences between a control-based and a risk-based approach to cybersecurity.
A control-based approach focuses on implementing specific security measures or controls to protect against known threats. This approach is often reactive, responding to threats as they occur.
On the other hand, a risk-based approach is proactive and strategic. It involves identifying potential risks, assessing their impact, and prioritizing security efforts based on the level of risk to the business.
This approach allows organizations to allocate their resources more effectively and focus on the threats that pose the most significant risk to business processes.
The Transition Process
Transitioning from a control-based to a risk-based cybersecurity program involves four key steps: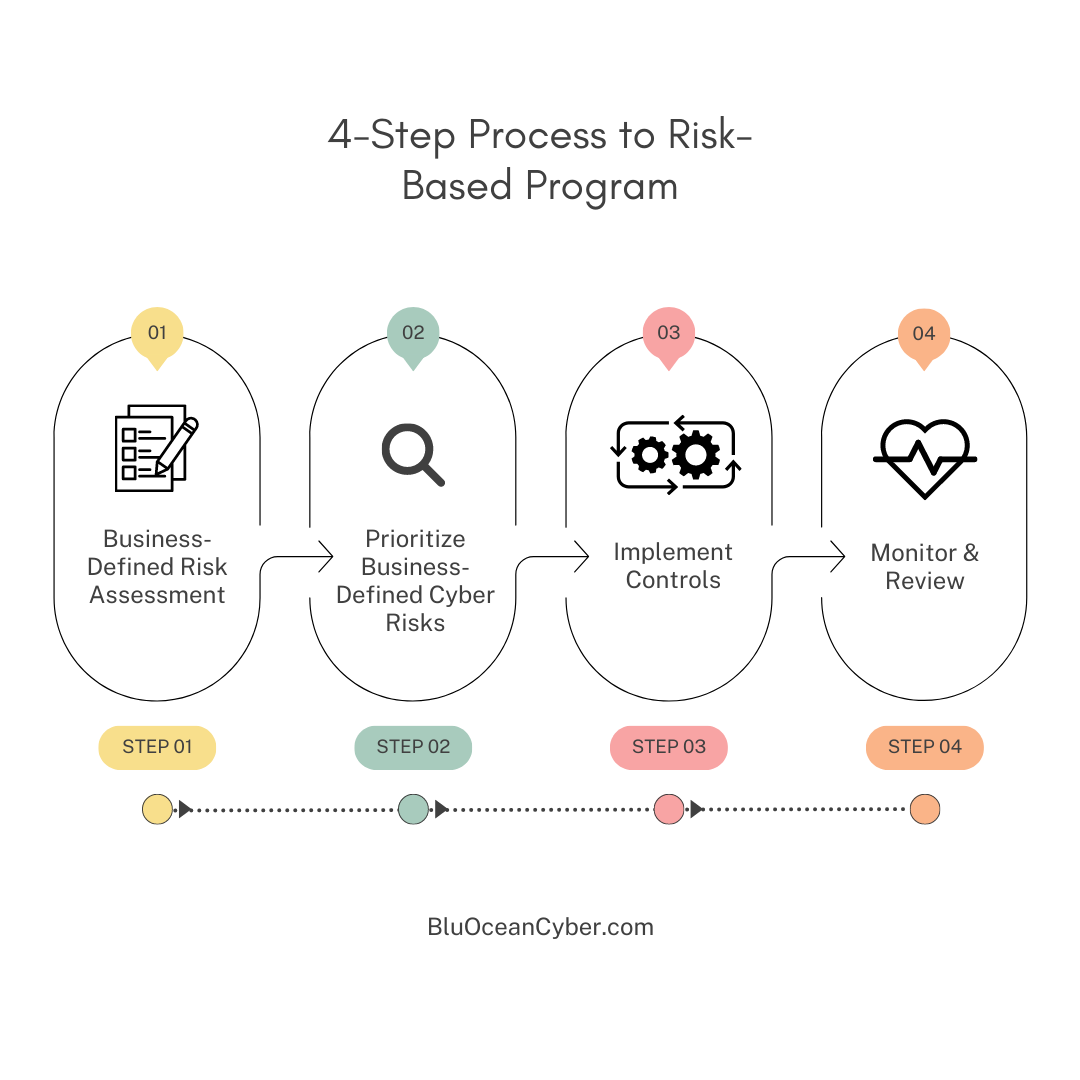
-
Business-Defined Risk Assessment: The initial and vital step in the transition process is positioning the business at the helm. This requires collaborating with leaders across various departments to pinpoint the significant cyber risks and the corresponding quantifiable risk thresholds acceptable to the business. A scenario-based approach should be adopted to identify specific cyber risks that resonate with them based on potential cyber events. By integrating pertinent threat-based scenarios, we empower the business to assess the impact of potential cyber risks and evaluate their probability. This approach fosters a more impactful, business-centric assessment of cyber risks, considering the organization’s unique priorities and concerns.
-
Prioritizing Business-Defined Cyber Risks: Once the risks have been identified and assessed, the next step is prioritizing them. This involves determining which business risks pose the greatest threat to the organization, the available budget and resources for addressing these risks, and other interdependencies like impending compliance deadlines to be met. Prioritizing risks allows organizations to allocate resources more effectively and focus on the most significant threats. Expertise from the business partners through conversation is necessary, with facilitation and support from the Chief Information Security Officer (CISO). Collaboration between the business and security teams is more critical than ever to properly prioritize cyber initiatives for managing risk to the company and stakeholders.
-
Implementing Controls: After the risks are prioritized, the next step is to implement controls to mitigate these risks. This may involve a range of measures, from technical controls such as firewalls and encryption, operational controls such as changes in business processes, to administrative controls such as policies and procedures.
-
Monitoring and Review: The final step in the transition process is ongoing monitoring and review. This involves regularly reviewing the effectiveness of the controls in place and making adjustments as necessary. It also involves continually reassessing business risks and adjusting priorities as new products and services are developed by the business and new threats emerge.
Join Thousands of Weekly Readers
Enter your email for instant access to our EXCLUSIVE ebook & discover the Roadmap for Moving to ROI-Led Cyber Risk Management.
Challenges in the Transition
Transitioning from a control-based to a risk-based cybersecurity program has its challenges.
One of the critical challenges is the need for a cultural shift within the organization. A risk-based approach requires a different mindset, proactive focused on business risks rather than reactive, mapping controls into business risks. The difference may appear nuanced. However, this is a major difference. This can be a significant hurdle, particularly in organizations where the control-based approach is deeply ingrained. The second major challenge is understanding the organization’s risk landscape better. A risk-based approach requires a deep understanding of the organization’s business strategy and processes, supporting technical infrastructure, threats specific to the organization, and their potential impact, and having a deep understanding of how adversaries look at their organization and associated business model and operations as a target for cybercrime. This requires significant time and resources and may require additional staff training, business and industry knowledge.
Finally, the risk-based approach requires greater collaboration and communication within the organization. It requires the involvement of key stakeholders from across the organization, from business end users to senior management, security engineers, the CISO, and support from your board of directors. This can be a challenge in organizations where cybersecurity is traditionally the sole responsibility of the IT department.
Overcoming the Challenges
Despite these challenges, there are several strategies that organizations can use to facilitate the transition to a risk-based cybersecurity program.

-
Education and Training: One of the most effective ways to overcome resistance to the risk-based approach is through education and training. This can shift the organizational culture and ensure that all stakeholders understand the outcomes and values of the risk-based approach.
-
Smart Collaboration: Encouraging collaboration between different departments can ensure that the risk-based approach is integrated into all aspects of the organization. This helps ensure that all stakeholders are involved in the process, significantly reducing friction and that the risk-based approach is aligned with achieving the organization’s overall business objectives.
-
Leveraging Technology: Technology can also facilitate the transition to a risk-based approach. Tools and platforms can simplify and automate the risk assessment process, making identifying and prioritizing risks easier. Technology can also aid in tracking remediation and risk reduction efforts to quantify the value of a risk-based approach.
-
Continuous Improvement: Finally, it’s important to remember that the transition to a risk-based approach is not a one-time event but an ongoing process. Regular reviews and updates can ensure that the approach remains effective and responsive to the evolving changes in business processes, products and services, and the emerging threat landscape.
Conclusion
Transitioning from a control-based to a risk-based cybersecurity program signifies more than a mere strategy shift; it represents a fundamental transformation in how organizations perceive and tackle cyber threats.
This change propels us from a technology-centric mindset to a business-led risk management approach. It encourages us to evolve from a reactive posture, where actions are taken post-incident, to a proactive stance, where potential business risks are anticipated, understood, and mitigated before they inflict damage. This shift equips organizations with greater resilience, adaptability, and preparedness for the ever-changing cyber threat landscape.
Such a transition aligns cybersecurity efforts with business objectives, enabling organizations to prioritize resources effectively. A risk-based approach enhances cybersecurity and contributes to overall business performance by minimizing potential disruptions and losses due to cyber incidents by focusing on high-risk areas that could significantly impact operations. As we traverse this digital battlefield, we must acknowledge that the dynamic nature of cybersecurity requires equally agile strategies. Though effective in its era, the control-based approach of the past may fall short of today’s sophisticated cyber adversaries. In this unending war for digital security, we must strengthen our defenses and adapt and innovate. Engaging with business leaders, understanding their concerns, and incorporating these insights into our strategies ensures our defenses are robust, relevant, and responsive to unique challenges.
Ultimately, while the battlefield is digital and the war is ceaseless, we can hold our ground and safeguard our digital assets with proactive strategies and the right approach. The cyber wars of tomorrow demand nothing less.