Published in ISACA Journal: https://www.isaca.org/resources/isaca-journal/issues/2022/volume-2/a-unified-response-to-cyberattacks-fraud-crime
These days, virtually all aspects of public life are visible online. With this trend comes abundant risk. Organizations are negatively affected more frequently by cyber-related issues, including cybersecurity intrusions, fraud and financial crimes (e.g., money laundering, bribery, tax evasion). Financial institutions may suffer greater impact from this trend, but other industries feel similar pain and may find lessons to learn.
Criminals are creative, inventive, and discover quickly what works and what does not. If customers are affected by nefarious activity, they do not care how the organization solves the problem as long as it is resolved promptly and effectively. Organizations must be prepared to rally their full resources; however, they often unintentionally dilute their efforts by handling cybersecurity, fraud and financial crimes in separate silos. A new approach is needed.
Illustrating the Problem
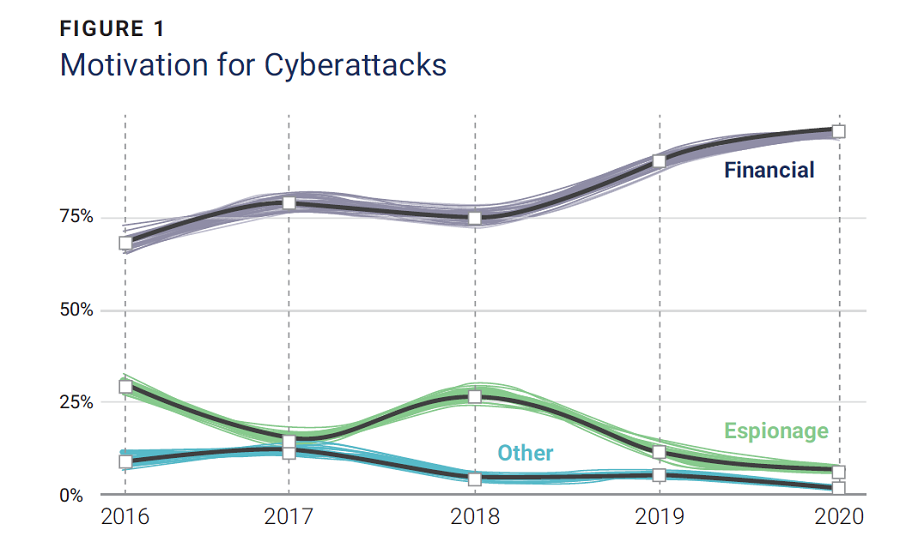
Although an enterprise’s outlay on cybersecurity is increasing at a staggering pace, the related crime numbers have not slowed and are instead surging.
Expenditures on cybersecurity products and services worldwide are expected to exceed US$1.75 trillion cumulatively from 2021 through 2025.2 According to the US Department of the Treasury’s Financial Crimes Enforcement Network, as of September 2020, enterprises across the United States lose a total of US$1 billion each month due to cybercrime.3 Such numbers are disconcerting by themselves, but they are even more so in cases of fraud, where additional losses from associated costs may exceed US$3 for every dollar stolen.4
Though numerous examples of cybercrime exist, one famous event is worth highlighting. In 2016, hackers attempted to steal US$1 billion from the Bangladesh Bank by focusing on SWIFT, the system through which banks transfer funds internationally.5 The hackers used custom-designed keylogger software to steal official bank credentials and a custom malware kit to cover their tracks. They monitored the bank’s activity and timed the transfers perfectly so that they would appear genuine. Only through a stroke of luck and a typographical error were the hacks discovered and partially stopped, with losses limited to US$101 million.6
Hackers have become familiar with cybersecurity vulnerabilities and banking processes, controls and possible attack points. They hold enterprises hostage through ransomware attacks. They steal confidential information, spoof identities and practice social engineering to gain access to and interruption of business operations. Their attempts are boundless.
Typical Approach to Managing Risk
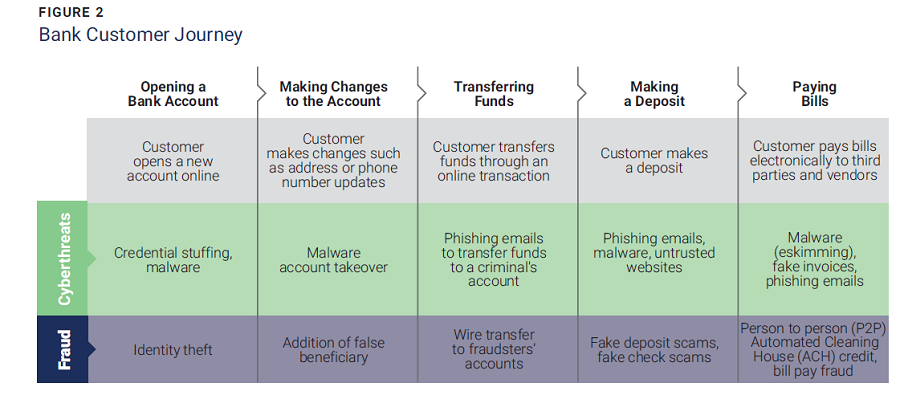
Protecting against risk in organizations requires a delicate balance. Consider the general customer journey in a bank (figure 2). Consumers have learned to trust the digital environment and engage in a purely online customer experience, forgoing human interaction with bank staff. The customer can open an account online by submitting vital information such as their name, address, phone number and Social Security number. Funds are deposited, managed and transferred (including payment of bills to third parties) via online processes. But each step leads to risk exposure.
Banks that can meet customer expectations of rapid, cohesive and safe customer experiences will benefit from increased revenue; in contrast, those that cannot will suffer from decreased value and lost business. To compete today, banks must find equilibrium between careful risk management and approving customer transactions in split seconds.
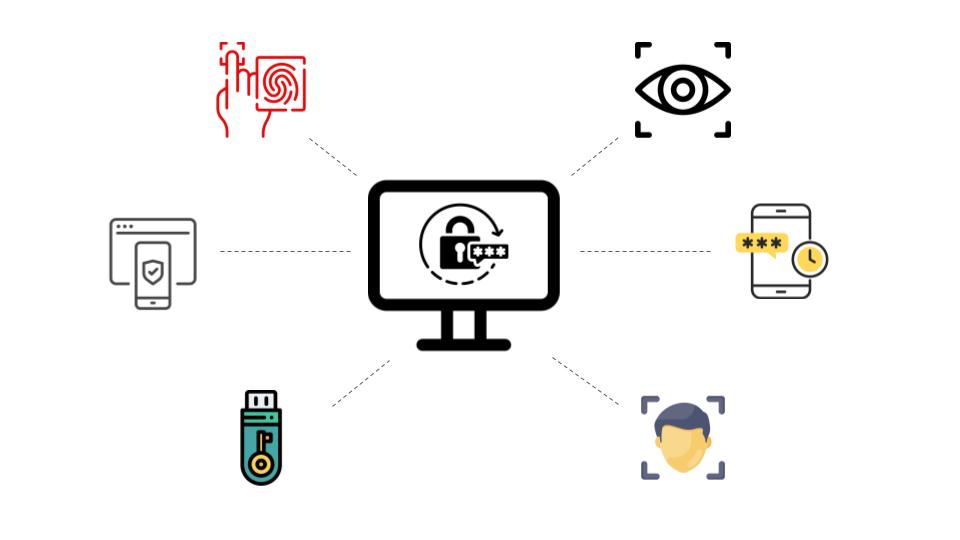
To keep user data and assets safe and secure, banks usually apply three types of countermeasures (figure 3):
-
Identifying and authenticating customers
-
Monitoring and detecting suspicious transactions and behaviors
-
Mitigating risk and issues
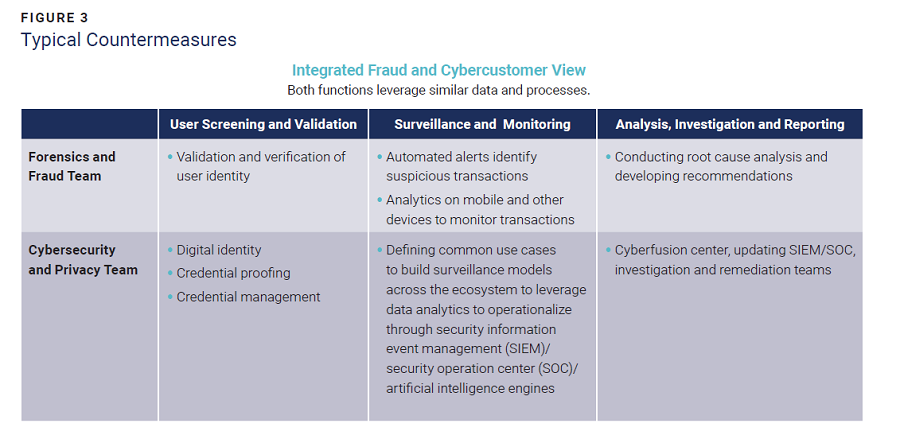
There is little distinction between the countermeasures in that they are applied regardless of the type of risk, whether it is for a cybersecurity breach, fraud or other financial crimes. Even so, these three types of risk are often managed by different departments in silos, each with its own tasks, responsibilities and accountabilities.
Criminals do not restrict themselves in this way. They attack at the most vulnerable access points, regardless of department. When banks make their weak spots more secure, cybercriminals moveto the next weakest point within the bank’s technological structure.
The increasing success of cyberattacks demonstrates the failure of the use of silos in protecting organizations. There is an urgent need for a simple but fundamental change.
Subscribe
Sign up with your email address to receive news and updates.
Integrated Approach to Risk Management
To more effectively and proactively protect their customers and assets, financial institutions should look at the three types of risk as a unified threat to the enterprise. They must take an outside-in approach that integrates coverage of cybersecurity, fraud and financial crimes. If separate departments are maintained (as opposed to merging all into one), enterprise management must foster collaboration by holding the individual departments equally accountable and tying rewards and penalties to unified outcomes. All departments should work jointly to reduce the risk to the organization while also helping drive better customer experiences. The more closely these departments can work (with the option of merging to a single entity), the more advantageous the results. Integration can save money, reduce gridlock among controls and enable innovation. It has also been shown to reduce the risk associated with cybercrime.7
Enterprises that have achieved a more complete integration are seeing benefits. One international bank chose to fully merge all crime-related operations and, as a result, has decreased its operating costs by approximately US$100 million while gaining a better understanding of beginning-to-end customer risk.8
To embark on this holistic journey, organizations must establish an integrated risk framework (figure 4) and assessment process by preparing a fundamental risk rating structure for the three risk types combined and then designing controls by leveraging a common set of data elements. The intention is to mitigate risk in alignment with the enterprise’s risk appetite and business strategy.
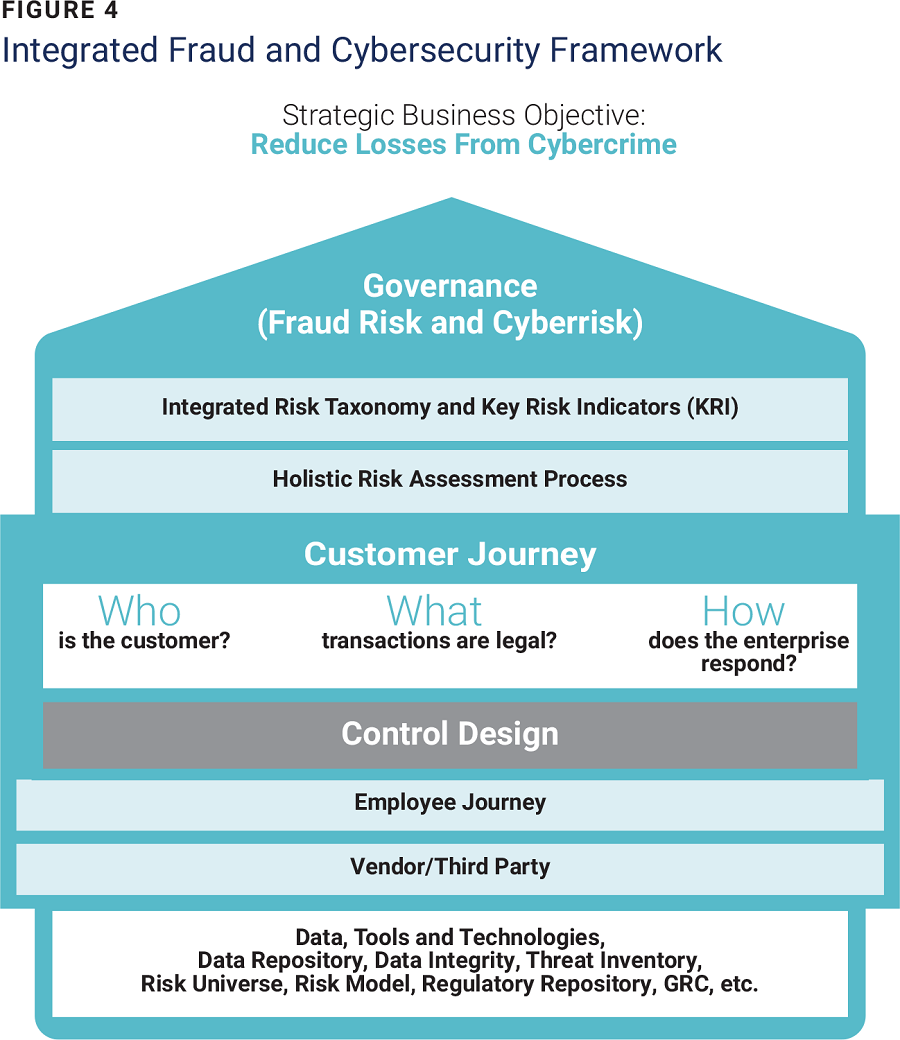
For example, consider the customer journey and business process of opening a bank account. First, the user’s identity must be validated to develop a secure self-registration process, and the fraud department should evaluate whether someone is creating fraudulent accounts. A holistic risk assessment approach encompasses both.
Threat countermeasures must be supported by solid analytics, providing insights for early detection and, in some cases, the prevention of cybercrime.
Artificial intelligence can enhance the analysis and combination of cyberthreat data (e.g., indications of compromise) and fraud/financial crime surveillance data.
Conclusion
A complete, holistic approach can be a more inclusive and effective way of reducing customer risk, lowering operating costs and improving the odds against cyberattacks, all leading to significant gains in customer trust.