Image Copyright © BluOcean Digital 2023
This futuristic-styled image showcases a cloud symbolizing SaaS platforms, surrounded by protective measures. Cybersecurity experts are ensuring its security, and the interconnected nodes in the background represent the vast digital network of SaaS applications.
CRM systems have evolved over the last two decades from a simple marketing campaign tool that stores user emails to an ecosystem of lead management, sales, commerce, services, user portals, and communities, storing sensitive user data to operate complex business processes.
Salesforce is a trusted leading CRM provider offering an extensive suite of products and solutions.
Let’s take a look at a typical Salesforce CRM implementation.
The procurement and business teams gather their requirements and identify the licenses to purchase. The technology teams and Salesforce administrators work together to implement the ecosystem (often involving consultants for expertise). Once the Salesforce clouds are configured, all your business data and sensitive user data are migrated to Salesforce. At any point so far, we haven’t involved the security teams to review the implementation and configuration or to ensure the data and user identities created on Salesforce’s client instance are following security best practices.
Understanding the Security Blindspot
There is clearly a big gap in addressing your business’s financial and regulatory risk from theft or disclosure of your critical and sensitive data.
So, who is managing this risk?
Is it fair to transfer back all the risk to the provider Salesforce?
All SaaS products, including CRM systems such as Salesforce, employ the Shared Responsibility Model, and the provider (here, ‘Salesforce’) is responsible for protecting only the backend infrastructure and application it provides.
All data hosted on this application, user identities created to provide access to this application, and monitoring and surveillance of cyber threats to this application still remain the client’s responsibility.
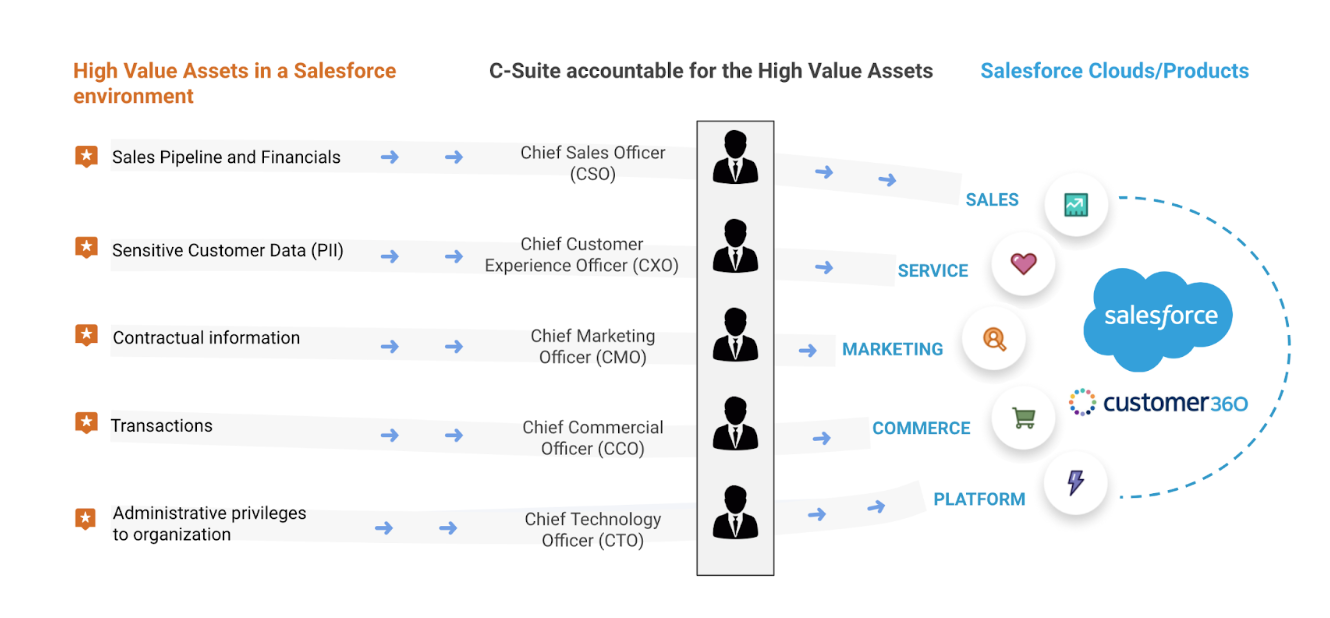
Who is Accepting the Risk?
So, if managing this financial and regulatory risk to our sensitive data is our responsibility, and we aren’t asking the security guys to manage this risk, then who is accepting this risk for the business? Well, like it or not,
- the Sales Head is accepting financial and material risk to business due to the loss of confidential sales and lead data, sales pipelines, and revenue forecasts;
- Chief Marketing Officer (CMO) is accepting regulatory fines and reputational risk to business due to theft of customer PII and sensitive contractual information;
- Commerce Chief is accepting operational and material risk to business and investors due to disclosure of all private business transactions;
- and Chief Technology Officer (CTO) is accepting financial and operational risk to the company due to the exploitation of administrative privileges provided to your internal systems via Salesforce integrations.
The Risk is Real & With a Great Potential Impact
The recent cyber attack at HCA impacting a whopping 11 million patient records proves that vulnerabilities and common oversights in third-party marketing software can lead to great losses.
Salesforce is a leading software in the marketing technology industry, and while they implement defense in depth in their infrastructure, it isn’t enough to protect your customer data in Salesforce.
Salesforce security is a crucial responsibility for the client to ensure their data and identities are secure from cyber-attacks and should be planned for during the implementation stage.
The Way Forward
Subject matter experts at BluOcean have been helping clients configure their Salesforce environment to secure their data and identities.
With lessons learned from clients of varying industries and tiers, we have designed a Salesforce Security reference architecture that helps cover all security gaps and blindspots in a Salesforce environment.
From BluOcean’s Salesforce Security Framework, we’ve handpicked a few topics of note and shared below a list of seven things you should know when configuring your production Salesforce environment.
Seven Misconfigurations in your Salesforce Instance that May Be Helping Cyber Attackers
Join Thousands of Weekly Readers
Enter your email for instant access to our EXCLUSIVE ebook & discover the Roadmap for Moving to ROI-Led Cyber Risk Management.
1. Implicit Sharing and Role Hierarchy
In Salesforce, by default, access to records is granted as per role hierarchies, i.e., records owned by a certain user can be accessed by everyone with a role higher in the hierarchy than the record owner.
While this default behavior helps manage access for standard objects and data, it can also lead to unintentional access grants for certain custom objects storing sensitive data.
Hence, the ‘Grant Access Using Hierarchies’ option should be disabled for custom objects that contain sensitive data.
2. Data Privacy and Anonymization
Salesforce provides a robust Privacy Center program for an organization’s data privacy requirements.
It helps track your customer’s consent changes, create policies that satisfy your customer’s right to be forgotten with the Right to Be Forgotten Policies feature or retain and de-identify a customer’s personally identifiable information (PII) using the Retention Policies feature.
You can even create Portability Policies that compile and deliver PII to customers in response to data subject access requests.
3. Cross-Cloud Encrypted Data Sharing
When shared with Marketing Cloud, sales or Service Cloud, encrypted data appears as unencrypted text or asterisks. The data appearance depends on the permissions of the user who completes the share through Marketing Cloud Connect.
For example, if User A has the View Encrypted Data permission in Sales Cloud and sends a report containing encrypted data, Marketing Cloud stores that encrypted data as regular text.
To resolve this,
- Users with permission to View Encrypted Data should not be assigned permission to share data across clouds.
- These fields can be re-encrypted in Marketing Cloud. Using Synchronized Data Sources, enable Field-Level Encryption permissions in Marketing Cloud to identify encrypted fields from Sales or Service Cloud. Then re-encrypt those fields in Marketing Cloud. Use this synchronized data in messages sent through Marketing Cloud.
4. Guest User Activation
When a new user is added to the Salesforce organization, an email with an activation link is shared. By default, Salesforce does not expire this activation link for seven days.
Whereas industry best practice advises expiring any new user link after 24 hours. If not configured manually, this session security setting can lead to session hijacking attacks.
5. Sharing Rules
Salesforce provides one of CRM systems’ most comprehensive security and sharing models. However, even after configuring security at the organization level, object level, field level, and record level, exceptions to access can be easily provided with Sharing Rules.
Users that do not own or have access to certain data from organization settings can still access this data if it is shared with them by data owners manually (directly with the user) or using Sharing Rules (shared with groups or roles assigned to the user).
This allows for a huge management vulnerability, which, if not administered effectively, can lead to unintentional disclosures of sensitive data.
6. Diluted Accountability
The ‘Log In As Any User’ option is provided by Salesforce so that administrators can log in as another user in their organization and help with emergency access or troubleshooting. However, unsupervised use of this feature can lead to diluted accountability.
All actions using the ‘login as any user’ control should be monitored via the Setup Audit trail.
7. Secure Apex Data Query
Salesforce has an extensive Apex developer community that helps extend custom functionalities over your Salesforce implementation. However, data protection concerns are common while querying data using Apex.
Additional settings must be embedded in queries to avoid unauthorized programmatic access to data that may be inaccessible to them on the Salesforce portal.
If all of these things are completely new information or you aren’t sure if your Salesforce environment is configured properly, BluOcean Salesforce Security specialists can guide you with understanding and implementing a robust Salesforce Security model.
Conclusion
CRM systems like Salesforce are vital to the way companies do business. Management and executives today place enormously valuable data in these systems without understanding the threat vectors, the increased attack surface, the risk with the valuable data, and the associated business impact. The C-Suite executives (Sales head, CMO, Chief Risk Officer, CTO, CIO) and product owners are pilots of company growth. It is time to switch seats and be co-pilots to security-led growth. Without proactive involvement and collaboration between security, business, and product teams, cyber-attacks and lawsuits will become common affairs, and all C-Suite executives and leaders will face the brunt of it. Businesses and leaders should ensure the Salesforce environment’s adoption, implementation, and expansion are driven by a security architecture and integrated into the enterprise risk management tools for ongoing security monitoring, detection, and response.