RJ Sangosti / Denver Post via Getty Images
A sinister shift is underway in a world where ‘cyberattacks’ have become synonymous with enterprise security.
Imagine a world where the tools of destruction are just a click away and accessible to anyone. Where DDoS and ransomware are not just threats but services available for purchase, and where the malevolent forces behind the screen have turned their gaze towards the most unsuspecting of victims – our schools, the nurturing grounds of our future, affecting not just the staff and students, but the very fabric of our families and society.
This has become a growing concern with the public, who finds it challenging to trust educational institutions with their personal information and their children’s welfare.
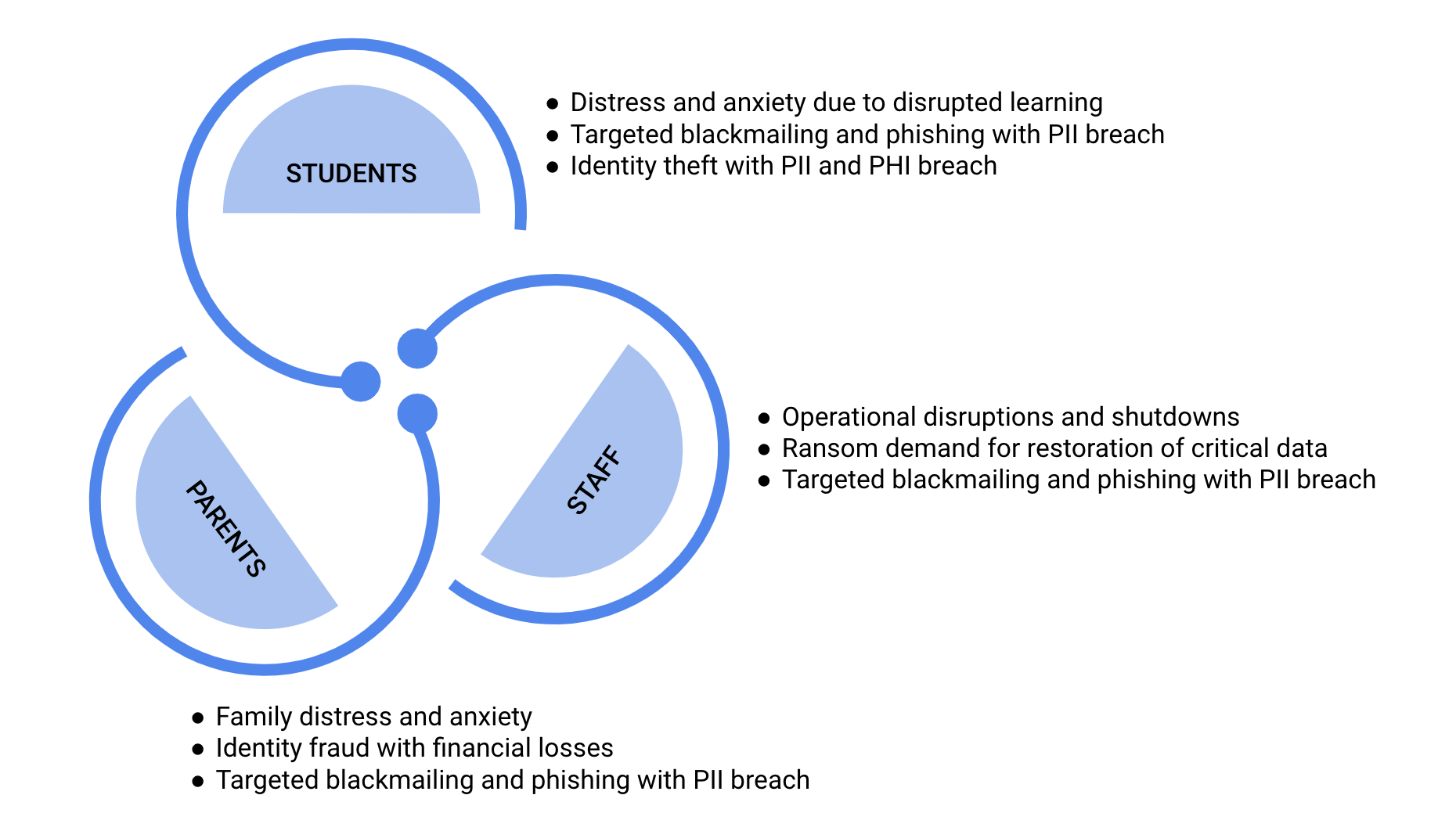
Imagine this scenario: a data breach in the school has led to the personal information of students and staff being sold on the dark web. This includes sensitive information including student grades, medical records, documented home issues, behavioral information, and financial information – of students, parents, and staff.
Malicious actors exploit this information to blackmail students for money and other gains.
Children are ill-prepared to manage these scenarios and frequently withhold information or refrain from seeking assistance due to concerns about their personal data being exposed online. This could result in a range of emotional and psychological impacts, including anxiety, stress, and emotional exhaustion in numerous cases.
The erosion of trust and confidence in the current education system has led to a setback in pursuing educational equity, with students from diverse backgrounds depending on e-learning tools and growing increasingly apprehensive about their potential detrimental effects.
As a nation, we have faltered if our educational and learning systems cannot safeguard our future generations, which is the most significant repercussion of cyberattacks on K-12 school systems today.
While financial, reputational, and regulatory losses are consequential, the primary drive for most government bodies and regulatory institutes, like CISA, is to protect diligent American families, and this is reflected in their ongoing efforts and support towards enhancing security in K-12 schools.
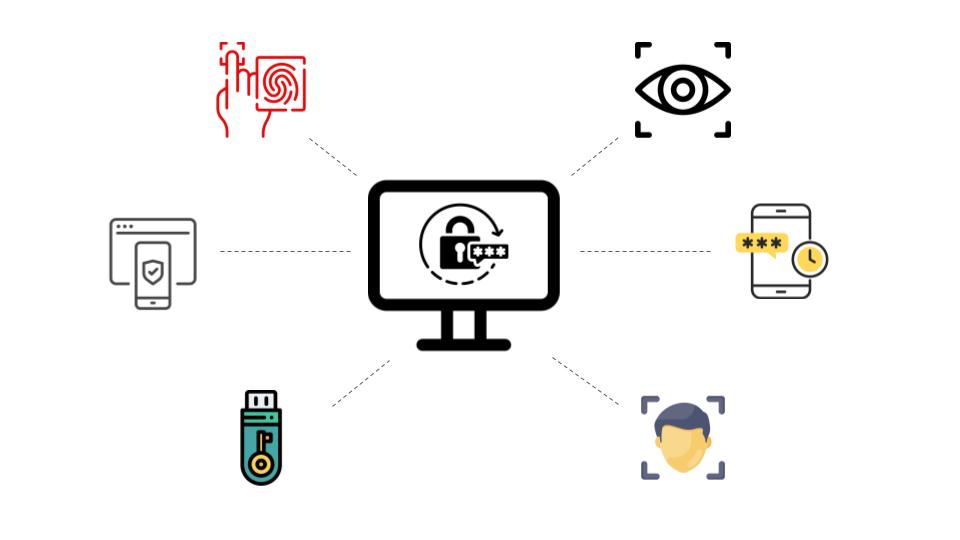
How Do K-12 School Systems Get Attacked?
In a series of recent attacks on August 14th, 2023, Prince George’s County Public Schools faced a broad network outage where 4500 of its accounts were impacted. All the students and employees were asked to reset their passwords, and operations were disrupted for multiple days.
This is the latest in a string of ransomware attacks in 2023, where dozens of schools in Minnesota, Iowa, West Virginia, California, Pennsylvania, New Hampshire, Arizona, Massachusetts, and others have grappled with disruptions and unauthorized access to sensitive student and staff information. Notably, there have been at least 48 instances of districts falling victim to ransomware attacks this year alone, surpassing the total count for the entirety of 2022 by three.
Another notable attack was on New Haven city schools, where hackers impersonated the city’s chief operating officer and private vendors in emails and successfully extracted $6 million in multiple payments. The issue came to light when a Connecticut school bus company raised concerns about non-payment of dues.
This is a classic example of business email compromise attacks where hackers get unauthorized access to your personal email, monitor the conversations, and then insert themselves as impersonators to complete fraudulent transactions.
Early 2020 saw a rise in Video Conference disruption attacks where uninvited malicious users verbally harassed students and teachers, displaying pornography and/or violent images, and doxing meeting attendees.
As per recent statistics, K-12 schools in the US have faced 1600 cyber incidents between 2016 and 2022.
Let’s take a look at the attack surface of a typical K-12 school system:
1. Endpoint Devices
With distance learning programs and tech-facilitated class delivery, every student and staff member carries devices (tablets, mobiles) in school. While these device endpoints may not store critical information, are an easy and often unprotected backdoor into the central network system. With the increase in devices, such as e-learning tablets, personal mobile phones, and school desktops, endpoint security has become a critical security measure.
2. Operational Technology (OT)
Traditionally, OT environments, including HVAC equipment, thermostats, lighting controls, and fire safety systems, had to be physically protected and were separated from IT. However, with more mature technology, most modern OT environments are tied to the internet and particularly vulnerable to ransomware attacks.
3. IT Systems
Student Information Systems (SIS), Learning Management Systems (LMS), Bus Routing and Transport Management tools, Inventory Management systems, and Financial and HR systems are some of the many IT systems used by every school and educational institution. These systems are often on-premise, which adds to the effort of continuously patching, monitoring, and securing them.
4. Collaboration and Conferencing Tools
Email and communication channels (Microsoft Teams, Slack, etc.), video conferencing platforms (Google Meet, Zoom, etc.), and Parent and Community engagement platforms are the SaaS technology landscape in every school system. While many significant players work to include security by design with these tools, schools need to configure them appropriately for secure use.
5. Human Resources
Just like enterprise security, school human resources are both an asset and a vulnerability. The human error factor is often exploited by threat actors in phishing and social engineering attacks to extract personal or sensitive information.
Join Thousands of Weekly Readers
Enter your email for instant access to our EXCLUSIVE ebook & discover the Roadmap for Moving to ROI-Led Cyber Risk Management.
Practical Strategies to Tackle Limited Resource Challenge
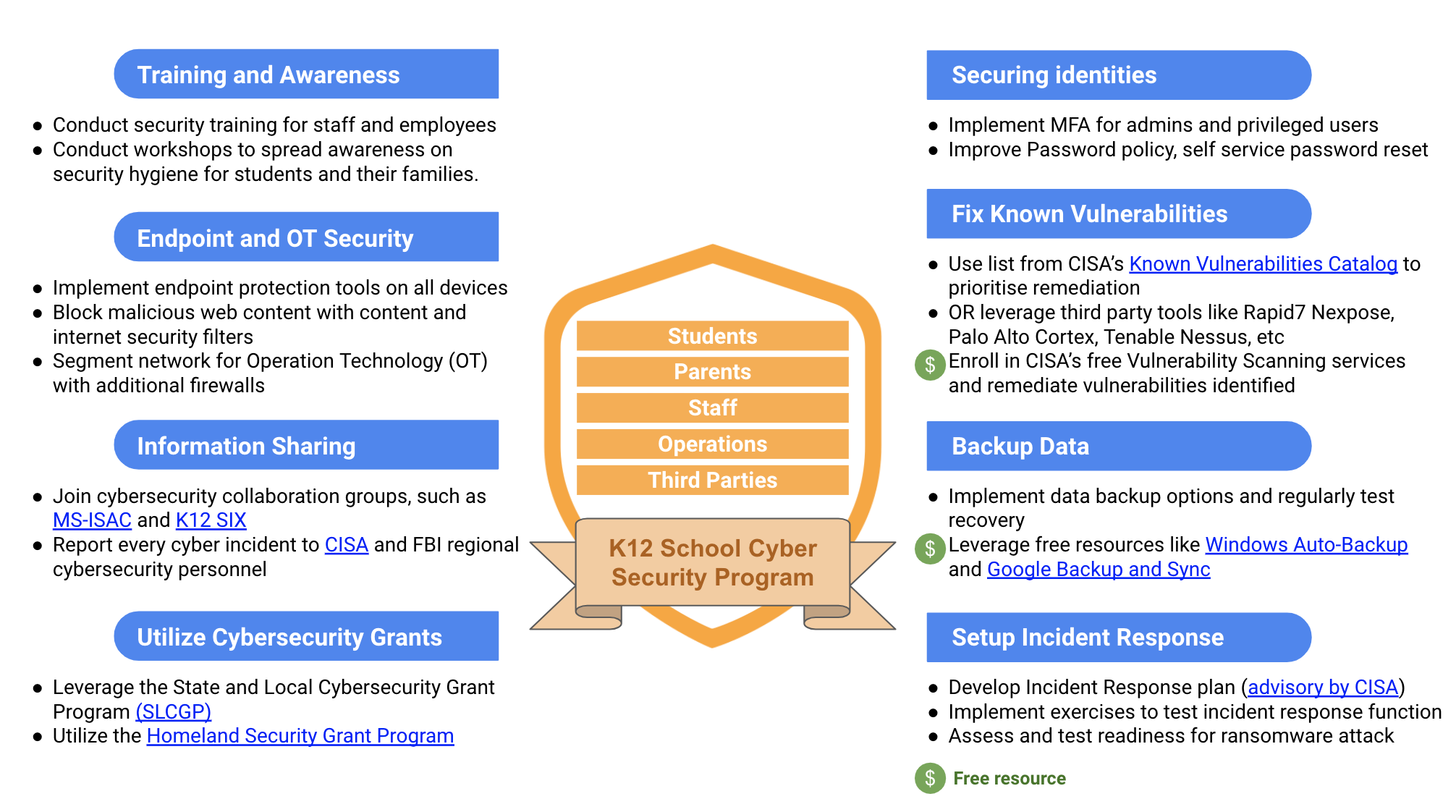
Schools and educational institutions may not have the deep pockets and extensive resources of large enterprises, yet the need for robust cybersecurity programs remains paramount to shield them from cyber attacks.
Here are some strategies that can guide schools in implementing cybersecurity controls effectively while optimizing costs and resource allocation:
1. On-Prem to Cloud
On-prem systems demand additional effort with patching systems, monitoring anomalous activity, and configuring security. A more manageable alternative is cloud solutions.
Many school management software providers have cloud-based solutions with subscription models. This reduces the effort required by school staff as the backend infrastructure is maintained, monitored, and secured by the cloud provider. It also optimizes cost as cloud-based solutions are highly scalable, and you pay only for what you use.
Schools should plan to transition IT systems to the cloud, wherever feasible, to save on both cost and effort.
2. Automation and Integrations
With multiple security controls implemented using different tools and technologies, monitoring and responding to intelligence has become resource-intensive. This effort grows multifold with the need to look at multiple dashboards generating multiple alert streams. Integrating all reporting into a single view and utilizing robotic process automation (RPA) for automated notifications, regular report exports, etc., can streamline monitoring efforts for security staff.
Incident Response, which is often supported by big SOC teams in enterprises, is another resource-intensive security function. However, not all events need manual response. Utilizing Security Orchestration, Automation, and Response (SOAR) runbooks can help automate analysis and the response of low-severity events, eventually reducing resource requirements for Incident Response.
3. Ask More From Technology Providers
K–12 organizations should expect the technology used for core educational functions like learning management and student administrative systems to have strong security controls enabled by default for no additional charge.
This requires a change in mindset and collaboration with other schools during the procurement process. Organizations like CISA have published advisories around this. During the technology procurement and renewal process, ensure that vendors do not charge more for security features like MFA and logs. Be especially aware of the “SSO tax,” the practice of charging customers more to connect a service (like a financial or timekeeping system) to the organization’s Single Sign On (SSO) portal.
As you become aware of upcharges for security features or unsafe defaults, start a dialog with other schools and ISAC members to assess a strategy for working together with the vendor to remediate.
Conclusion
Against this backdrop, an alarming sequence of cyber incidents underscores the vulnerability of K-12 educational systems. These institutions face many threats, from weak devices and operational technology to critical IT systems and staff information. Despite limited resources, practical cybersecurity strategies can help. Switching to cloud-based solutions can reduce the need for complex in-house maintenance. Using automation and integrating technology smartly can also boost security efforts. Recognizing the vital link between education and security should push schools to tackle this challenge. By strengthening their defenses, they not only protect their own operations but also restore trust in the foundation of our society.