Image via Forbes Newsletters
As 2023 is about to end, we embark on a new journey in the cyber world yet again. As we stand into the unfolding landscape of 2024, it is important to look into the intricate dance between technology and security that has shaped the preceding year. While the advancements in technology have brought unprecedented levels of connectivity and innovation, they have also opened new doors to various malicious actors.
Throughout the year, organizations struggled with a wide array of cyber risks, ranging from hundreds of millions of dollars in financial losses to completely inoperable operations, in the case of hospitals barring patient admissions and surgeries. The continuity of remote work only intensified the battleground, as the threat actor has adapted itself to exploit vulnerabilities created by the rise of decentralized workforce.
Even in this storm, there is still a glimmer of hope. Technological advancements in the field of Artificial Intelligence and Machine Learning are providing a more proactive and intelligent defense to digital assets. Even regulatory frameworks are evolving with changing threat landscapes to hold organizations accountable for their cybersecurity posture. The ongoing battle between defenders and attackers continues, as new technologies have brought both opportunities and risks.
Now as we move towards 2024, it is crucial to learn the lessons from the preceding year. This blog aims to delve into the emerging cyber risk trends of 2024, providing insights and actionable strategies to navigate this ever-evolving landscape.
Join Thousands of Weekly Readers
Enter your email for instant access to our EXCLUSIVE ebook & discover the Roadmap for Moving to ROI-Led Cyber Risk Management.
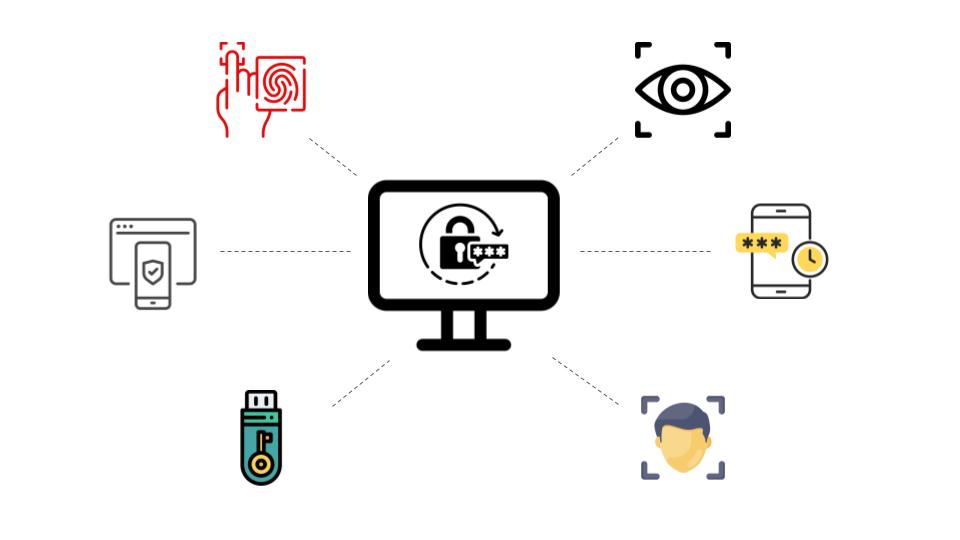
New Cybersecurity Attack Vectors
This year we saw numerous attacks with attack vectors like ransomware, phishing, stolen credentials, misconfigurations, and vulnerability exploits. While these attack vectors are not new to the threat landscape, their evolution and adaptation to the changing digital world have led to some noteworthy trends. Let’s take a look at what we saw this year and what we expect to see going into 2024.

Image Copyright © BluOcean Digital 2023
Trends to Watch for in 2024
1. Generative AI Adopted on Both Sides of the Battle

Image via Acceleration Economy
With the rise of OpenAI’s ChatGPT, AI has been a hot topic on everyone’s mind as tech giants race to develop their own LLMs and AI integrations. Near the end of this year it was recorded that 91% of leading organizations were investing in AI activities.1 AI creates boundless opportunities for the technology landscape, but also introduces unforeseen cyber risks. The presence of AI cannot be ignored by organizations as the demand for adoption rises. Organizations can capitalize on accelerated growth and operations with the help of AI, but must keep the associated risk in mind. On the other hand AI will both help and hinder attackers with evolving technology to both exploit and protect.
Organizations are eager to adopt AI technologies to increase productivity and automate workflows, but they need to take into account the potential for destructive cyber consequences. Many of the AI tools in place are new to the market and we have not seen what kind of cyber attacks and zero day vulnerabilities they may encounter. This means companies carry more responsibility in understanding and securing these technologies with the right controls. This may also mean more training for employees on what data to use within AI to combat insider threats. Companies also need to take into consideration privacy and regulatory risks of using these tools and carefully examine their scope and use internally to avoid potential regulatory and legal consequences.
Just as enterprises are quickly adopting AI tools into their technology stack, hackers are using AI to level up their attacks too. AI tools allow for hackers to create wide scale phishing and fraud campaigns including deep fakes for easier social engineering and deception. Organizations must stay vigilant and increase awareness and training among their employees to not fall victim to these evolving and elaborate attempts. Attackers may also use AI tools to easily automate malware that may not be detected by most antivirus software. Companies must be wary as security tools adapt to these attacks and work to implement defense in depth to decrease the impact of any successful attacks.
2. Evolution of Phishing Attacks

Image via Tech Republic
Phishing is often considered low hanging fruit for preventing breaches and adding layered protections. However we continue to see attackers using social engineering as an initial attack vector to compromise major enterprises. The group Scattered Spider compromised both MGM Resorts and Caesars Entertainment by using social engineering tactics on IT help desks and gaining access to employee accounts. Both of these attacks caused significant damage and class action lawsuits that followed. It does not seem like this attack vector will cease any time soon or ever and hackers tactics only continue to mature.
Hackers are perfecting their craft and uplevelling using AI and deepfakes to better impersonate their targets. Deepfake technology can be used to mimic voices over the phone to easily fool IT help desks and other unsuspecting victims. AI is also allowing hackers to create new phishing campaigns at mass scale and speed creating increasingly convincing emails sent to more victims. We expect to see these AI driven attacks to evolve and become more convincing in the coming year.
Many believe that by implementing two factor authentication they will thwart all phishing attacks but attackers have been evolving their tactics to new technologies, Hackers do not see MFA as a blocker, they see it as just another hurdle to entry. They are capitalizing on organizations using one time passwords by convincing users to disclose them or hacking their emails to gain access to them. For organizations using authentication apps they have taken to spamming users with MFA requests when they have stolen credentials in hopes they will become fatigued and accept the requests It is proving that two factor authentication and basic phishing training is not enough any more and strategically placed multifactor authentication and security awareness must be implemented to avoid critical impact.
3. Zero Trust Security and the SaaS Enterprise

Image via Akamai
As digital transformations continue and cloud technology dominates, we have seen more and more organizations working towards a zero trust digital environment. The long lasting effects of the pandemic and the rise of the remote workforce has pushed enterprises to eliminate on-premise networks and rely on cloud and SaaS technologies. The continued use and reliance on SaaS products for critical business processes has led more organizations to build towards a zero trust model and in 2024 we believe we will continue to see this expand across industries. While this transformation is allowing for major strides in security by eliminating many perimeter threats and leveraging the least access privilege, we are seeing new and evolving security threats organizations need to adapt to.
As more cloud and SaaS technologies are adopted, third party risk has skyrocketed for numerous organizations. 81 percent of organizations had sensitive SaaS data exposed.Many SaaS providers continue to be breached, exposing their customers’ organizations and leading to breaches with multiple levels of disclosure.
These breaches are leading to increased legal and regulatory complexity. Organizations must also take into account downtime of SaaS tools if they are compromised and incur an incident, and carefully map interdependencies while creating recovery plans in case of third party failure. Organizations must carefully procure SaaS providers and understand that they are taking on increasing levels of risk as their technology stack expands.
Join Thousands of Weekly Readers
Enter your email for instant access to our EXCLUSIVE ebook & discover the Roadmap for Moving to ROI-Led Cyber Risk Management.
Now vetting vendors before implementation is only the first step to securing zero trust environments. Organizations are learning that just using SaaS does not ensure that you are secure. However this realization is coming after adoption of numerous technologies and vendors, and we are predicting that there will be an urgency to retroactively secure these softwares. Insecure configurations are rampant across SaaS tools and gaining visibility post implementation is difficult, similar to challenges with on-premise infrastructure. We see the rise of securing the “SaaS enterprise” a challenge that organizations will grapple with in 2024 and beyond.
4. Destructive Attacks Against Business Operations

Image via aNetworks
We have written about many attacks this year noting a shift in the narrative, with cyber attackers targeting key business processes and disrupting operations. Notable attacks include MGM Resorts, Caesars Entertainment, Clorox, and Johnson Controls where not only data was compromised but key business processes were stalled for days and even weeks. The destruction is expanding far beyond class action lawsuits and regulatory fines. Companies continue to incur steep drops to their share prices and lost revenue from weeks of stalled business operations. In 2024 we predict that organizations will broaden their lens of security protections, moving from protecting sensitive data to building business resilience.
As the SEC Rule on Material Incident Disclosure and Cyber Risk Management is enforced, we expect to see more and more incidents like these disclosed to the public. Organizations’ security faults will come into the public eye at a much earlier date than anticipated and companies must balance restoring business operations as well as the backlash from public disclosure. Attackers now have a new avenue of attacks where they can make the news without even touching sensitive information and we expect a significant increase of ransomware attacks in frequency targeting business operations and ransom demands in the coming year. This will be paired with increasing pressure from boards demanding more information on these kinds of cyber risks that CISOs may not be able to answer.
5. Board and Business and Security as Collaborators

Image via TS2
As mentioned in the prior trend in 2023, we have seen the importance of security growing to become a business priority. Security is becoming a regular agenda item in board meetings as investor concerns grow with constant cyber attacks making the news. Top down governance of cyber risk management is a need for companies to be able to properly secure their organizations and board and business buy-in is a key first step. Regulators are taking note of this as well. The SEC Rule on Material Incident Disclosure and Cyber Risk Management and NYDFS Amended Cybersecurity Rule as well as others are now requiring disclosure on board and senior management oversight of cyber risk. In 2024 organizations will need to harbor meaningful collaboration bringing the CEO, business leaders, and cyber leaders to the same table to make risk based investment decisions.
Alongside regulatory requirements CISOs are receiving more pressure from their boards to deliver answers about cyber risk impact on the business. New questions are being asked about financial and operational impacts that will force CISOs to become more deeply integrated with business processes. In addition, the new SEC rule, requires organizations to disclose any cyber incident that may materially affect business strategy, results of operations, or financial condition.The public and regulators have taken note that poor cyber posture can have a significant impact on shareholder value and companies may now pay the price if they are not fully transparent. This push for protection of investors and shareholders again is pushing security in the spotlight of business executives. In the coming year we expect to see the potential for large fines issued from the SEC and that organizations will slowly begin to learn and adapt their security strategy to be more business centric.
With all the pressures from emerging regulations and persistent cyber threats, paired with increased visibility from business leaders, we expect that cyber budgets may be expanding across the board even with the current economic circumstances. Companies are beginning to realize that investing in their protective controls alone may actually lead to far more financial harm than their cost. However given the economic environment and state of digital transformation, we may see more investments in strategic controls especially those surrounding SaaS environments.
Going Forward…
With the emergence of these technologies and threat landscape, paired with increased regulatory pressures, we expect to see a noteworthy and potentially tumultuous future in the cybersecurity landscape in 2024 and beyond. We believe these trends could bring many consequences.
- Attackers are more motivated to interrupt and damage business operations in attacks, so we expect attackers to aim to take down major operations for greater financial and operational impact.
- Consequences of attacks may become more expensive in the aftermath with regulatory consequences and hallmark lawsuits coming forward with the implementation of the SEC rule, like SEC v. Solarwinds.
- New and evolving threat vectors that pair with advances in technology like MFA evasion, attacks on SaaS, and zero day exploits especially on AI softwares.
- Regulators may begin to navigate the world of AI and GenAI and we could see drafted rules and regulations to comply with in the near future.
However with all these changes, we also expect to see some positive consequences in the security realm.
- Boards may become more equipped with high skilled security professionals as regulatory demands increase.
- Businesses may take more ownership and initiative with their organization’s security strategy in efforts to reduce the risk from potential attacks on their key processes.
- Budgets and investments in security may expand as top down support grows and vendors may adapt and mature their products to match.
- CISOs may be forced to transform their roles to become more business centric from board demands, both a challenging and exciting prospect for security executives.
Join Thousands of Weekly Readers
Enter your email for instant access to our EXCLUSIVE ebook & discover the Roadmap for Moving to ROI-Led Cyber Risk Management.
The world of security is ever changing and always surprising. In 2024 we look forward to the possibilities of new technologies while preparing for the threats that may lie ahead. To try and predict the future in cyber security is nearly impossible but we are confident that we will all learn and grow in the year ahead. BluOcean looks forward to a new year of helping organizations build resilient defenses to create a more secure future for all.
Sources
- Techopedia. (n.d.). Artificial Intelligence (AI) – Statistics.Techopedia.
- Varonis. (n.d.). SaaS Data Risk Report.Varonis Blog.
- Marr, B. (2023, October 11). The 10 Biggest Cyber Security Trends in 2024 Everyone Must Be Ready For Now.Forbes.
- Splashtop. (n.d.). Cybersecurity Trends and Predictions for 2024.Splashtop Blog.
- LinkedIn. (n.d.). 10 Biggest Cyber Security Trends in 2024 Which Everyone Should Be Ready For.LinkedIn.
- Dark Reading. (n.d.). Cyber Threats to Watch Out for in 2024.Dark Reading.
- Balbix. (n.d.). Attack Vectors and Breach Methods.Balbix Insights.
- Digital Transformation Australia. (n.d.). Current Cyber Security Threat Landscape.Digital Transformation Australia.
Written by : Katie Reilly, Smaranava Roy